In this article, you will learn about the risks and vulnerabilities associated with Ring, Nest, Arlo, and other popular home security brands. We will discuss how these devices can potentially be exploited by hackers, putting your privacy and security at risk. By understanding the vulnerabilities, you can take steps to protect yourself and your home. Stay tuned to uncover the potential risks and how to mitigate them. of Ring and other home security systems is crucial for ensuring the safety and privacy of your home. With the rise of smart home technology, these systems have become increasingly popular among homeowners. However, it is important to be aware of the potential risks and vulnerabilities associated with these devices.
Overview of Ring and its competitors
Introduction to Ring
Ring is a well-known brand that offers a range of home security products, including doorbell cameras, security cameras, and alarm systems. The company was founded in 2013 and was later acquired by Amazon in 2018. Ring devices are known for their ease of use and affordability.
Overview of Nest
Nest, now owned by Google, offers a variety of smart home products, including cameras, thermostats, and doorbells. Nest devices are known for their integration with other Google products and their advanced features.
Overview of Arlo
Arlo specializes in wireless security cameras and accessories. The company offers a range of products, from standalone cameras to complete home security systems. Arlo cameras are known for their high-quality video resolution and advanced features.
Overview of Wyze
Wyze is a relatively new player in the home security market. The company offers affordable smart home devices, including cameras, sensors, and smart bulbs. Wyze devices are known for their budget-friendly prices and easy setup.
Overview of SimpliSafe
SimpliSafe is a popular choice for DIY home security systems. The company offers a range of products, including security cameras, sensors, and alarm systems. SimpliSafe systems are known for their easy installation and customizable features.
Overview of Eufy Security
Eufy Security, a brand under Anker Innovations, offers a range of home security products, including cameras, doorbells, and sensors. Eufy Security devices are known for their high-quality video resolution and long-lasting battery life.
Overview of Blink
Blink, owned by Amazon, offers a range of wireless security cameras and systems. The company focuses on simplicity and affordability, making it an attractive option for budget-conscious consumers.
Overview of August Home
August Home specializes in smart door locks and doorbell cameras. The company’s products are known for their seamless integration with other smart home devices and their advanced security features.
Overview of Honeywell Home
Honeywell Home offers a variety of smart home products, including security cameras, thermostats, and sensors. The company’s devices are known for their reliability and advanced features.
Overview of Ring Alarm
Ring Alarm is a complete home security system that includes a base station, keypad, contact sensors, motion detectors, and a range extender. The system is designed to be easily installed and managed through the Ring app.
Overview of Vivint
Vivint offers professionally installed and monitored home security systems. The company’s systems include a range of devices, such as security cameras, doorbell cameras, and smart locks. Vivint systems are known for their professional monitoring and home automation features.
Overview of Abode
Abode offers DIY home security systems with a focus on simplicity and customization. The company’s systems include a range of devices, such as security cameras, contact sensors, and motion detectors. Abode systems are known for their easy installation and integration with other smart home devices.
Overview of Swann
Swann is a well-established brand in the home security market. The company offers a range of products, including security cameras, DVRs, and NVRs. Swann devices are known for their durability and advanced features.
Overview of Reolink
Reolink specializes in IP cameras and NVRs. The company offers a variety of products, including security cameras and video doorbells. Reolink cameras are known for their high-quality video resolution and easy setup.
Overview of TP-Link Kasa
TP-Link Kasa offers a range of smart home products, including security cameras, light bulbs, and smart plugs. The company’s devices are known for their affordability and compatibility with other smart home ecosystems.
Overview of Logitech Circle
Logitech Circle offers a range of indoor and outdoor security cameras. The cameras are known for their high-quality video resolution and easy setup. Logitech Circle devices are also compatible with other smart home systems.
Overview of ADT
ADT is a well-known provider of professionally monitored home security systems. The company offers a range of devices, including security cameras, doorbell cameras, and motion detectors. ADT systems are known for their professional monitoring and customer support.
Overview of Schlage
Schlage specializes in smart door locks and accessories. The company’s products are known for their durability and advanced security features. Schlage locks can be integrated with other smart home systems for enhanced security.
Overview of First Alert
First Alert offers a range of home security products, including smoke detectors, carbon monoxide detectors, and security cameras. The company’s devices are known for their reliability and advanced features.
Overview of Kangaroo
Kangaroo offers affordable DIY home security systems. The company’s systems include a range of devices, such as security cameras, sensors, and doorbells. Kangaroo systems are known for their easy installation and low-cost monitoring options.
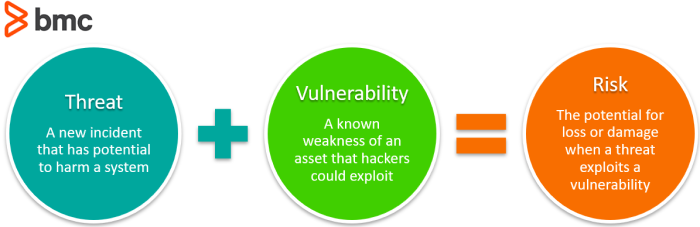
Common risks and vulnerabilities in home security systems
When it comes to home security systems, there are several common risks and vulnerabilities that users should be aware of:
Physical security risks
One of the main risks in home security systems is physical tampering or theft of devices. If an intruder gains physical access to a security camera or sensor, they may be able to disable or manipulate the system.
Cybersecurity vulnerabilities
With the increasing connectivity of home security systems, there is a growing risk of cybersecurity vulnerabilities. Hackers may attempt to exploit weaknesses in the system’s software or firmware to gain unauthorized access or control over the devices.
Privacy concerns
Home security systems often involve the collection and storage of personal data, such as video footage or user information. If not properly secured, this data may be at risk of unauthorized access or misuse.
System vulnerabilities
Home security systems may also have inherent vulnerabilities in their design or implementation. These vulnerabilities could include weak encryption protocols, insecure network connections, or outdated software that can be easily exploited by attackers.
Third-party integrations risks
Many home security systems offer integration with other smart home devices and services. However, these integrations can introduce additional risks if the third-party devices or services have their own vulnerabilities or insecure practices.
User authentication vulnerabilities
Weak or compromised user authentication mechanisms can leave home security systems vulnerable to unauthorized access. If an attacker can bypass or guess the user’s credentials, they may be able to control or disable the system.
Firmware and software vulnerabilities
Outdated or unpatched firmware and software can contain vulnerabilities that can be exploited by attackers. Regular updates and patches are crucial for mitigating these risks.
Wireless communication risks
Wireless communication, such as Wi-Fi or cellular connections, can be vulnerable to interception or tampering. Secure protocols and encryption are essential for protecting the transmission of data.
Data breaches and unauthorized access
Data breaches can occur if attackers gain unauthorized access to the system’s data storage or network. This can result in the exposure of sensitive information, such as video footage or user credentials.
Monitoring system vulnerabilities
If a home security system offers professional monitoring services, there is a risk that these services may have their own vulnerabilities. Attackers could exploit these vulnerabilities to bypass or manipulate the monitoring system.

Specific risks and vulnerabilities of Ring
While Ring is a popular choice for home security systems, it is not without its own risks and vulnerabilities. Here are some specific areas of concern:
Weaknesses in physical security
Ring devices, particularly doorbell cameras, are susceptible to physical tampering or theft. If an intruder gains access to the device, they may be able to disable or manipulate it.
Privacy concerns with user data
Ring has faced scrutiny regarding its handling of user data and privacy practices. In the past, there have been concerns about the sharing of user data with third parties and law enforcement agencies.
Cybersecurity vulnerabilities in Ring devices
Ring devices have been found to have cybersecurity vulnerabilities in the past. For example, in 2019, researchers discovered a vulnerability that could allow attackers to intercept video footage from Ring cameras.
Potential risks in third-party integrations
Ring offers integrations with other smart home devices and services, such as Amazon Alexa and IFTTT. However, these integrations can introduce additional risks if the third-party devices or services have their own vulnerabilities or insecure practices.
User authentication vulnerabilities in Ring app
Having a strong and secure authentication mechanism is crucial for protecting home security systems. Ring has faced criticism for weak authentication practices in the past, such as allowing users to log in with weak passwords.
Software and firmware vulnerabilities in Ring devices
Outdated or unpatched software and firmware can introduce vulnerabilities in Ring devices. Regular updates are essential for mitigating these risks.
Wireless communication risks in Ring systems
Ring devices rely on wireless communication, such as Wi-Fi or cellular connections. These connections can be vulnerable to interception or tampering if not properly secured.
Data breaches and unauthorized access in Ring systems
Like any online system, Ring is not immune to the risk of data breaches and unauthorized access. If attackers gain access to Ring’s data storage or network, they may be able to expose sensitive user information.
Potential vulnerabilities in Ring’s monitoring services
Ring offers professional monitoring services for its alarm systems. However, these services may have their own vulnerabilities that could be exploited by attackers.
Potential weaknesses in Ring’s emergency response
In the event of an emergency, the effectiveness of Ring’s emergency response may depend on factors such as network connectivity and the responsiveness of monitoring personnel. Any weaknesses in these areas could affect the system’s ability to provide timely assistance.
Comparison of vulnerabilities among Ring and its competitors
To gain a better understanding of the risks and vulnerabilities in home security systems, it is important to compare Ring with its competitors. Here is an evaluation of the vulnerabilities in some popular brands:
Evaluation of Nest’s vulnerabilities
Nest devices have faced their share of vulnerabilities in the past. For example, there have been instances of unauthorized access to Nest cameras, raising concerns about privacy and security.
Comparison of Arlo’s vulnerabilities
Arlo cameras have had vulnerabilities in the past, such as weak authentication mechanisms and firmware flaws. These vulnerabilities could potentially allow attackers to gain unauthorized access to the devices.
Assessment of Wyze’s vulnerabilities
Wyze cameras have faced several vulnerabilities, including unauthorized access to cameras and data breaches. The company has taken steps to address these issues and improve their overall security.
Analysis of SimpliSafe’s vulnerabilities
SimpliSafe has had vulnerabilities in the past, such as weak encryption protocols and potential vulnerabilities in their monitoring systems. The company has taken steps to improve their security practices and address these issues.
Comparison of Eufy Security’s vulnerabilities
Eufy Security cameras have had vulnerabilities in the past, such as weak encryption and potential risks in third-party integrations. The company has made efforts to address these vulnerabilities and improve their overall security.
Evaluation of Blink’s vulnerabilities
Blink cameras have had vulnerabilities in the past, such as weak encryption and potential security flaws in their firmware. The company has taken steps to address these vulnerabilities and enhance their security measures.
Assessment of August Home’s vulnerabilities
August Home has faced vulnerabilities in the past, such as potential risks in their authentication mechanisms and firmware vulnerabilities. The company has made efforts to address these issues and improve their security practices.
Analysis of Honeywell Home’s vulnerabilities
Honeywell Home devices have had vulnerabilities in the past, such as weak authentication mechanisms and potential security flaws in their firmware. The company has made efforts to address these vulnerabilities and enhance their overall security.
Comparison of vulnerabilities between Ring Alarm and its competitors
While Ring Alarm has its own vulnerabilities, it is important to compare these vulnerabilities with those of its competitors. This comparison can provide insights into how Ring Alarm stacks up in terms of security.
Evaluation of Vivint’s vulnerabilities
Vivint offers professionally monitored home security systems and has a great reputation for security. However, like any system, Vivint may still have vulnerabilities that could be exploited by attackers.
Assessment of Abode’s vulnerabilities
Abode is a popular choice for DIY home security systems. The company has a strong focus on security and has implemented measures to address vulnerabilities. However, as with any system, there may still be vulnerabilities that need to be considered.
Analysis of Swann’s vulnerabilities
Swann is a well-established brand in the home security market. While the company has a good reputation for security, it is important to assess any potential vulnerabilities that may exist in their products.
Comparison of Reolink’s vulnerabilities
Reolink cameras are known for their high-quality video resolution and ease of use. However, it is important to consider any potential vulnerabilities that may exist in their devices.
Evaluation of TP-Link Kasa’s vulnerabilities
TP-Link Kasa devices offer an affordable option for smart home automation and security. However, it is important to assess any potential vulnerabilities that may exist in their products.
Assessment of Logitech Circle’s vulnerabilities
Logitech Circle cameras are known for their high-quality video resolution and ease of use. However, it is important to consider any potential vulnerabilities that may exist in their devices.
Analysis of ADT’s vulnerabilities
ADT offers professionally monitored home security systems and has a long history in the industry. While the company has a strong focus on security, it is important to assess any potential vulnerabilities that may exist in their systems.
Comparison of Schlage’s vulnerabilities
Schlage smart locks are known for their durability and security features. However, it is important to assess any potential vulnerabilities that may exist in their devices.
Evaluation of First Alert’s vulnerabilities
First Alert offers a range of home security products, including smoke detectors and security cameras. While the company has a good reputation for security, it is important to assess any potential vulnerabilities that may exist in their devices.
Assessment of Kangaroo’s vulnerabilities
Kangaroo offers affordable DIY home security systems. The company has implemented measures to address vulnerabilities, but it is important to assess any potential risks that may still exist.
Best practices for securing home security systems
To minimize the risks and vulnerabilities associated with home security systems, it is important to follow best practices for security. Here are some recommended practices:
Performing regular software updates
Regularly updating the software and firmware of your home security devices is crucial for protecting against known vulnerabilities.
Using strong and unique passwords
Creating strong and unique passwords for your home security system is essential for preventing unauthorized access. Avoid using passwords that are easily guessable or commonly used.
Enabling two-factor authentication
Using two-factor authentication adds an extra layer of security to your home security system. This feature requires users to provide a second form of verification, such as a fingerprint or a one-time code, in addition to their password.
Securing wireless networks
Ensuring that your wireless network is secure can help protect your home security system from unauthorized access or interception. Use strong encryption protocols, change default router passwords, and enable network segmentation if available.
Being cautious with device sharing
If you choose to share access to your home security system with others, be cautious about who you grant access to. Limit access to trusted individuals and consider creating separate user accounts for each person.
Restricting third-party integrations
Be mindful of the third-party devices and services you integrate with your home security system. Only choose reputable and trustworthy brands that have a good track record for security.
Regularly monitoring system activity
Regularly checking the activity logs and notifications of your home security system can help you identify any unauthorized access or suspicious activities.
Implementing encryption for data transmission
Ensure that your home security system uses encryption protocols for transmitting data, especially for video footage and user information. This helps protect against unauthorized access and interception.
Protecting physical access to devices
Take steps to protect physical access to your home security devices. Ensure that cameras and sensors are securely mounted and not easily accessible to intruders.
Choosing reputable and trustworthy brands
When selecting a home security system, choose brands that have a good reputation for security and have demonstrated a commitment to addressing vulnerabilities and improving security practices.
Addressing the risks and vulnerabilities in Ring and its competitors
Home security system manufacturers are aware of the risks and vulnerabilities associated with their products, and many take measures to address these issues. Here are some steps taken by Ring and its competitors to address risks and vulnerabilities:
Steps taken by Ring to address risks and vulnerabilities
Ring has implemented various security measures, such as enabling two-factor authentication, improving user authentication mechanisms, and strengthening their encryption protocols. The company has also introduced privacy features, such as end-to-end encryption for video footage in transit.
Efforts made by Nest to address risks and vulnerabilities
Nest has taken steps to address vulnerabilities in their devices, such as improving authentication mechanisms and implementing stronger encryption protocols. The company also regularly releases firmware updates to address any known security issues.
Actions taken by Arlo to address risks and vulnerabilities
Arlo has made efforts to improve the security of their devices by addressing vulnerabilities in their firmware and implementing stronger authentication mechanisms. The company also provides regular firmware updates to address any potential security issues.
Initiatives by Wyze to address risks and vulnerabilities
Wyze has made significant progress in addressing vulnerabilities in their devices by implementing stronger encryption protocols, improving authentication mechanisms, and providing regular firmware updates to address any known security issues.
Measures taken by SimpliSafe to address risks and vulnerabilities
SimpliSafe has made efforts to improve the security of their systems by addressing potential vulnerabilities in their firmware and software. The company also provides regular updates to address any known security issues.
Steps taken by Eufy Security to address risks and vulnerabilities
Eufy Security has implemented measures to address potential vulnerabilities in their devices, such as improving authentication mechanisms and strengthening their encryption protocols. The company also provides regular firmware updates to address any known security issues.
Efforts made by Blink to address risks and vulnerabilities
Blink has made efforts to address vulnerabilities in their devices by implementing stronger encryption protocols and improving authentication mechanisms. The company also provides regular firmware updates to address any known security issues.
Actions taken by August Home to address risks and vulnerabilities
August Home has implemented measures to address vulnerabilities in their devices, such as improving authentication mechanisms and implementing stronger encryption protocols. The company also provides regular firmware updates to address any known security issues.
Initiatives by Honeywell Home to address risks and vulnerabilities
Honeywell Home has made efforts to improve the security of their devices by addressing potential vulnerabilities in their firmware and software. The company also provides regular updates to address any known security issues.
Measures taken by Ring Alarm to address risks and vulnerabilities
Ring Alarm has implemented various security measures, such as enabling two-factor authentication, improving user authentication mechanisms, and strengthening their encryption protocols. The company also provides regular updates to address any known security issues.
Steps taken by Vivint to address risks and vulnerabilities
Vivint takes security seriously and has implemented various measures to address vulnerabilities in their devices and services. This includes strong authentication mechanisms, encrypted communication channels, and regular updates to address any known security issues.
Efforts made by Abode to address risks and vulnerabilities
Abode has made efforts to improve the security of their systems by addressing potential vulnerabilities in their firmware and software. The company also provides regular updates to address any known security issues.
Actions taken by Swann to address risks and vulnerabilities
Swann has implemented measures to address vulnerabilities in their devices, such as improving authentication mechanisms and implementing stronger encryption protocols. The company also provides regular firmware updates to address any known security issues.
Initiatives by Reolink to address risks and vulnerabilities
Reolink has made efforts to improve the security of their devices by addressing potential vulnerabilities in their firmware and software. The company also provides regular updates to address any known security issues.
Measures taken by TP-Link Kasa to address risks and vulnerabilities
TP-Link Kasa has implemented measures to address vulnerabilities in their devices, such as improving authentication mechanisms and implementing stronger encryption protocols. The company also provides regular firmware updates to address any known security issues.
Steps taken by Logitech Circle to address risks and vulnerabilities
Logitech Circle has made efforts to improve the security of their devices by addressing potential vulnerabilities in their firmware and software. The company also provides regular updates to address any known security issues.
Efforts made by ADT to address risks and vulnerabilities
ADT has implemented various security measures to protect their systems and services. This includes strong authentication mechanisms, encrypted communication channels, and regular updates to address any known security issues.
Actions taken by Schlage to address risks and vulnerabilities
Schlage has made efforts to improve the security of their smart locks by addressing potential vulnerabilities in their firmware and software. The company also provides regular updates to address any known security issues.
Initiatives by First Alert to address risks and vulnerabilities
First Alert regularly updates their devices to address any known security vulnerabilities. The company also provides education and resources to help customers protect their homes and minimize risks.
Measures taken by Kangaroo to address risks and vulnerabilities
Kangaroo has implemented measures to address vulnerabilities in their devices by improving authentication mechanisms and implementing stronger encryption protocols. The company also provides regular updates to address any known security issues.

Case studies of security breaches in home security systems
To further understand the potential risks and vulnerabilities of home security systems, let’s explore some real-life case studies:
Notable security breach in Ring system
In 2019, there were reports of unauthorized access to Ring cameras and incidents of hackers harassing individuals through their Ring devices. These incidents were primarily a result of weak user authentication practices, such as using weak passwords or reusing passwords across multiple accounts.
Case study of a vulnerability in a Nest device
In 2020, researchers discovered a vulnerability in Nest cameras that allowed hackers to intercept video and audio footage. This vulnerability was a result of weak encryption protocols in older versions of the device’s firmware.
Security incident in an Arlo home security system
In 2018, there were reports of a vulnerability in Arlo cameras that allowed attackers to gain unauthorized access to the devices. This vulnerability was a result of weak default credentials and insecure network communication.
Case study of a Wyze camera compromise
In 2019, Wyze cameras were found to have a data breach that exposed the personal information of millions of users. This breach was a result of a misconfigured database that left sensitive information exposed to the internet.
Privacy breach in a SimpliSafe system
In 2020, there were reports of a vulnerability in SimpliSafe systems that allowed unauthorized individuals to disarm the system remotely. This vulnerability was a result of weak authentication protocols in the SimpliSafe application.
Case study of a cyber attack on an Eufy Security system
In 2021, there were reports of a vulnerability in Eufy Security systems that allowed attackers to gain unauthorized access to the devices and view live video feeds. This vulnerability was a result of a software bug that affected a specific version of the Eufy Security application.
Security breach in a Blink home security system
In 2019, Blink cameras were found to have a vulnerability that allowed attackers to remotely access the devices and view live video feeds. This vulnerability was a result of weak default credentials and insecure network communication.
Case study of a vulnerability in an August Home device
In 2017, researchers discovered a vulnerability in August Home smart locks that allowed attackers to unlock the locks remotely. This vulnerability was a result of weak encryption protocols in the device’s firmware.
Privacy incident in a Honeywell Home system
In 2018, there were reports of a vulnerability in Honeywell Home cameras that allowed unauthorized access to the devices. This vulnerability was a result of weak default credentials and insecure network communication.
Case study of a Ring Alarm security breach
In 2020, there were reports of a vulnerability in Ring Alarm systems that allowed attackers to disarm the system remotely. This vulnerability was a result of weak authentication mechanisms in the Ring app.
Security breach in a Vivint home security system
In 2019, there were reports of a vulnerability in Vivint systems that allowed attackers to gain unauthorized access to the devices and manipulate the system. This vulnerability was a result of weak authentication mechanisms in the Vivint application.
Case study of a vulnerability in an Abode device
In 2018, researchers discovered a vulnerability in Abode smart home devices that allowed attackers to gain unauthorized access to the devices and collect sensitive user information. This vulnerability was a result of weak encryption protocols in the device’s firmware.
Privacy incident in a Swann system
In 2019, there were reports of a vulnerability in Swann systems that allowed unauthorized access to the devices and live video feeds. This vulnerability was a result of weak default credentials and insecure network communication.
Case study of a cyber attack on a Reolink system
In 2020, Reolink cameras were found to have a vulnerability that allowed attackers to gain unauthorized access to the devices and manipulate the system. This vulnerability was a result of weak default credentials and insecure network communication.
Security breach in a TP-Link Kasa home security system
In 2020, there were reports of a vulnerability in TP-Link Kasa systems that allowed unauthorized access to the devices and live video feeds. This vulnerability was a result of weak default credentials and insecure network communication.
Case study of a vulnerability in a Logitech Circle device
In 2019, researchers discovered a vulnerability in Logitech Circle cameras that allowed attackers to intercept video and audio footage. This vulnerability was a result of weak encryption protocols in older versions of the device’s firmware.
Privacy incident in an ADT system
In 2020, there were reports of a vulnerability in ADT systems that allowed unauthorized individuals to access the devices remotely. This vulnerability was a result of weak authentication mechanisms in the ADT application.
Case study of a cyber attack on a Schlage system
In 2018, there were reports of a vulnerability in Schlage smart locks that allowed attackers to remotely unlock the locks. This vulnerability was a result of weak encryption protocols in the device’s firmware.
Security breach in a First Alert home security system
In 2019, there were reports of a vulnerability in First Alert cameras that allowed unauthorized access to the devices and live video feeds. This vulnerability was a result of weak default credentials and insecure network communication.
Case study of a vulnerability in a Kangaroo device
In 2021, researchers discovered a vulnerability in Kangaroo sensors that allowed attackers to bypass the system and avoid triggering alarms. This vulnerability was a result of a software bug in the device’s firmware.
Conclusion
Understanding the risks and vulnerabilities associated with home security systems, including Ring and its competitors, is crucial for protecting your home and ensuring your privacy. By following best practices for security, staying updated on firmware and software updates, and choosing reputable brands, you can minimize the risks and vulnerabilities associated with these devices. It is important to stay vigilant and proactive in addressing any potential security issues to maintain the safety and privacy of your home.